The Ultimate Open Wifi Sniffer

- Listens on channels 1, 6, and 11 simultaneously
- Only logs plaintext http traffic and wpa handshakes
- Logs into organized timestampted files
- Starts logging on boot without any interaction
- Scans for 60 seconds all networks around into csv file
- 24/7 uptime capable
Abstract
I love networking projects, so I wanted a cool little device that would boot up and start listening for plain text http traffic. I originally wanted to do this with a raspberry pi, but had some serious issues with drivers and trying to get three of the usb interfaces working at once. However, on an orange pi PC, it worked no problem out of the box with the 3 at once.
Details
In terms of hardware, I used an orange pi PC and 3 TP LINK TL-WN722N USB wifi adapters with upgraded antennas:

The upgraded antennas give it a much narrower signal vision, but can pick up much further signals. This image shows how it works perfectly:
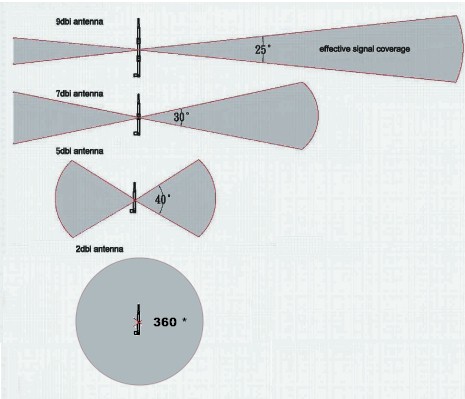
For software I used a combination of the aircrack-ng suite and tshark to accomplish this task. I used the aircrack-ng suite to put my usb interfaces into monitor mode and to do the 60 second capture of wifi networks into a csv file like so:
timeout 60s airodump-ng -c 1,6,11 wlan0mon -w info
I used tshark to decrypt the open wifi traffic and filter out just http. However, tshark cannot actually run a filter on a live capture, so I had to do something strange and run tcpdump and pipe it into tshark like so:
tcpdump -i wlan0mon -n -w - | tshark -F pcap -r - -o wlan.enable_decryption:true -l -Y "http.request" -w 1.cap
While this seems like a strange way to go about it, it actually works well and I’m glad with the results. Here is how I only logged the wpa handshakes:
tcpdump -i wlan0mon -n -w - | tshark -F pcap -r - -l -Y "eapol" -w HAND-1.cap
Automation
From there, I just wrote a script that starts all interfaces in monitor mode at boot, and started three commands like the one listed about in screens. Before it starts the screen however, it runs an airodump-ng command to just gather csv info on wireless access points around it, scanning for 60 seconds.
Then I set up a cron-job that actually kills the screens and restarts them because the way t-shark works is that it keeps track of lots of packet information which eventually consumes all memory, so I have to kill it every 5 hours (arbitrary choice) and restart it in a new time-marked folder (runs a script called refresh.sh). Another hack-y fix, but works well and it sorts the packets into convenient folders anyway.
Offloading the Data
Then, once I want to offload the data, I just attach the ethernet to my laptop (Orange Pi PC is acting as a DHCP server), and run a script I made called “combineAll.sh.”
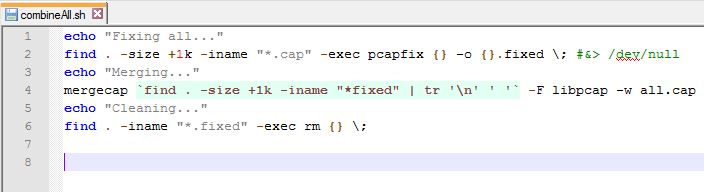
The script runs a tool called pcapfix to make sure all the cap files are formatted correctly, then runes mergecap on all of them to combine them all into a single all.cap that can then be copied off.
Shortcomings
I do love the orange pi PC, it was relatively cheap. For some reason works perfectly with the drivers to allow 3 USB to wifi adapters while the raspberry pi didn’t no matter how hard I tried. However, quite surprisingly, it does not take micro-usb power. It actually works on a radial DC power plug like the ones that go into your router. This is fine for if you have an outlet nearby, but if you are on the go, you can’t use a USB power bank. I even made a makeshift USB to gpio power, however the support cables I used were too thin to support the current and the orange pi couldn’t bring up all 3 interfaces:

Now, it’s also obvious that most websites these days use https, so the device doesn’t capture much. It just captures random connectivity checks and random stuff for the most part, but a large amount of sites still use plaintext http, so it is still worthwhile, perhaps not for much longer though.
Also, a problem is that since the orange pi pc is running without a connection to the internet, whenever it boots, it’s time is wrong, so the date stamps are not the actual time, but still are accurate relative to it’s offset.
Comment to let me know any shortcomings you see as well, and ideas on how to make it better in any way. I’d love to hear your thoughts.
A Note on Legality
One should always exercise caution when sniffing anything that does not belong to you (obviously). I do not condone such behavior and leave that responsibility and decision up to the user. However, there have been legal decisions declaring sniffing open wifi legal. I encourage you to find further reading in the following (slightly outdated) articles:
http://blog.privatewifi.com/federal-judge-rules-that-wifi-sniffing-is-perfectly-legal/