MitM Rpi Passive Ethernet Sniffer
In the movies you might have seen those devices spys place to sniff a computers network connection by sitting in the middle of their ethernet connection. I thought this would be cool to do and it turned out to be super easy to do with the right commands on a raspberry pi. There are also some awesome very practical uses for something so low cost and cheap to run like this.

The Raspberry pi I setup has two ethernet interfaces (and a wireless one as a bonus, broadcasting a wifi hotspot). It uses the on board one built into the board, and a external usb to ethernet adapter that was recognized by the Pi no problem out of the box as eth1.
Pi Setup
I made a small script that can be run at boot by putting it in /etc/rc.local which sets up the two interfaces to allow traffic to flow right through it:
createbr.sh:
ifconfig eth0 0.0.0.0
ifconfig eth1 0.0.0.0
echo "1" > /proc/sys/net/ipv4/ip_forward
brctl addbr bridge0
brctl addif bridge0 eth0
brctl addif bridge0 eth1
ifconfig bridge0 10.0.0.110 netmask 255.255.255.0
ifconfig bridge0 up
Now we still have our two eth0 and eth1 interfaces that look like this:
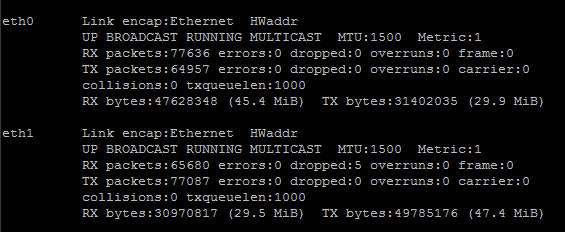
However now we also have our special bridge0 interface that looks like this:
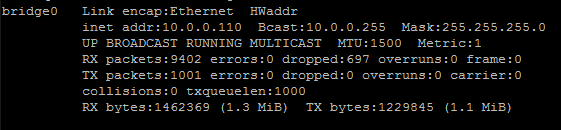
Now the cool thing is that 10.0.0.110 is now our pi’s ip address that can be connected to from _either _eth0 _or _eth1.
Now if we connect a victim computer in between it’s connection to the switch:
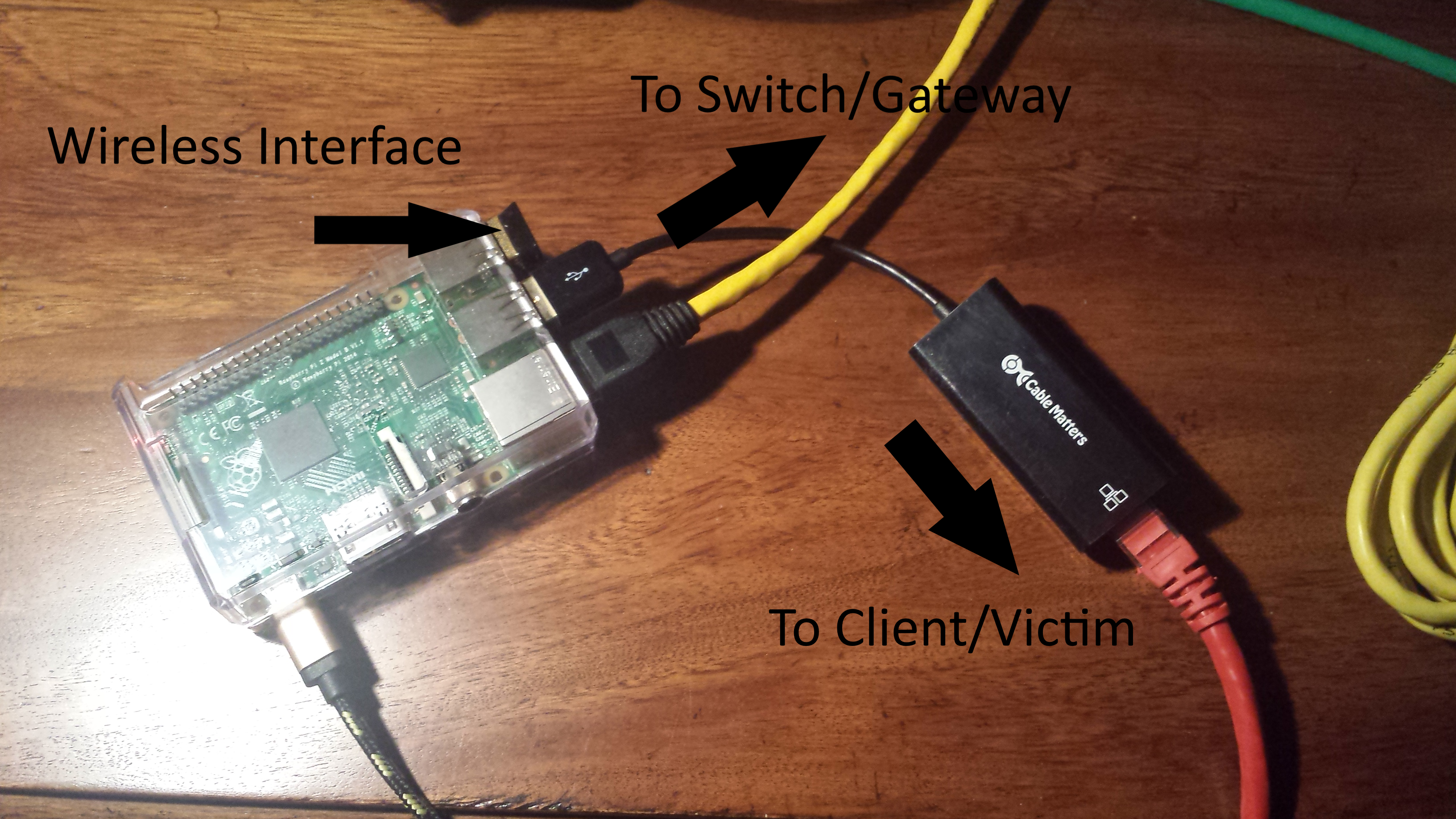
The Rpi can now see all traffic going through! So if we run a simple tcpdump command:
tcpdump -n -s 0 -w sniff.cap -i bridge0
We see all traffic from the victim computer! (truncated)
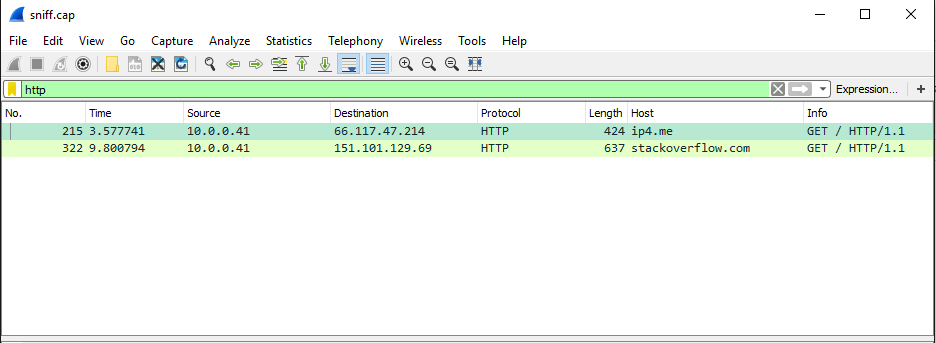
Now unless you are on the same network as the victim (to connect to the pi through 10.0.0.110), you can’t really access the files until you retrieve the device. However the cool part is I have a wifi interface that uses hostapd and isc-dhcp-server that acts as a fully working wifi access point. So after this device is planted, it can be remotely connected to and used to download the capture files, just like a spy~!
Practical Uses
There are a few awesome practical uses for this. Imagine just installing snort, the Intrusion Detection System, and listening over the bridge! You could catch some sketchy traffic you didn’t know about leaving or entering your computer. You could also set up a low cost firewall of course, or spam filter, or web filter. You could even make a parental control system that shuts off the internet after a certain time using a cronjob that runs:
ifconfig bridge0 down
At 10pm, then brings it back up at 8am or something. You could even get clever and shut off the internet only for your kids by adding an ip table rule that denies all traffic except a few mac addresses of your own devices. Comment if you think of another cool use!
Lessons
This can even be scaled up greatly (given you hopefully have a quad core Pi 2 or 3, imagine putting this between a subnets uplink to the router or internet. You may not be able to see intranet traffic between LAN computers, but anything going to the outside world then would be captured by the Pi!
This small devices goes to show the importance of physical security when it comes to ethernet. This device is unseen in any traceroute command through it, and if you assigned an address like 0.0.0.0 to the bridge, it would be totally invisible! Especially if you disable the wifi hotspot and just retrieve the device later, the device is undetectable! However if you think there is a way to detect this device, please let me know in the comments! I’d love to hear about it.
All it needs is a proper black box and it’s good to go!
###