How Facebook hacked themselves
This post used to be called “How I “Hacked” A Facebook Account - Kinda” However I have since renamed it since really facebook is the one that messed up and I just noticed it.
This one had me scratching my head. To my own disbelief, I gained full access to a Facebook account I had no username/password to, and I will tell you how it happened.
Disclaimer: I get some may not identify this as “hacking.” Please realize that while I didn’t actively exploit something, this should NOT have happened, and it is arguably worse than a vulnerability because I got access to this persons facebook basically just given to me. Read about how it happened:
The Setup
I love doing networking stuff, so one weekend I was doing a test in which I did a long time exposure to network traffic on my wireless home network. I set up a device similar to my Ultimate Open Wifi Sniffer and let it run for a few days. It captured all wireless data on channels 1,6, and 11 (not only open wifi like in the other project). I concatenated the files together in a way I detail in the other project. Since I obviously know the password to my home network, I could decrypt the my home network traffic using airdecap-ng.
As usually, I opened them up in wireshark. Now of course there was a lot of random and encrypted useless data that it captured, so I applied some of my favorite filters like http.host, and the http.cookie.
The Find
Found some standard random stuff, session cookies for random non-encrypted websites but wait what…..
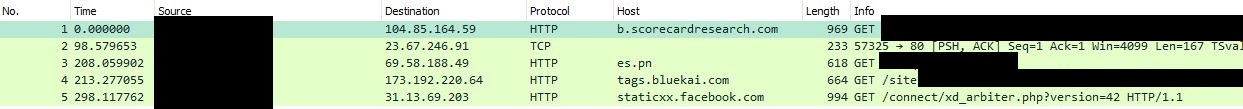
What’s this…
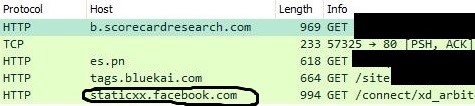
There shouldn’t be cookies associated with fetching static facebook content…
What’s Staticxx?
For those of you that don’t know, a lot of static content delivered by big companies (icons, app images, website pictures, etc.) that aren’t specific to users delivered over a Content Delivery Network (CDN). This allows them to put these images on servers all around the world, allowing them to load faster (picking a closer server and reducing load on the primary servers). This is why if you log in to your bank from the other side of the globe as their HQ, the pictures and everything may load fast, but your actual data will take extra time (it is fetched from their main server).
So, when fetching these static images and content, you need not send your session cookies (what identifies you when you log in) each time, because anyone can get these images, they are public! In addition, they are usually not sent over encrypted means because…well…there is no need to encrypt them, they are public!
Something Isn’t Right…
So why in the world would this static request have cookies associated with it…
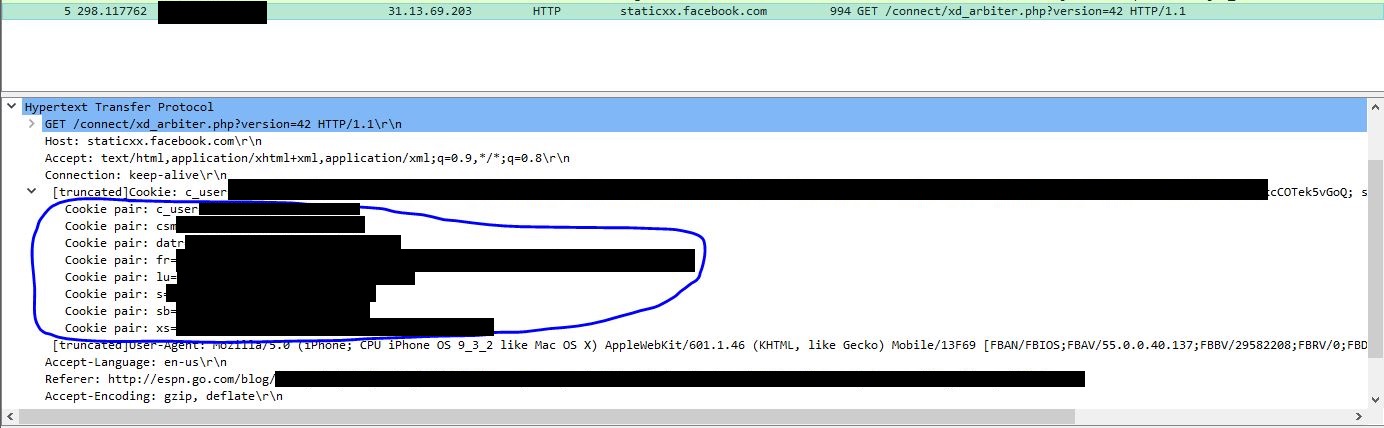
No way…these are persistent cookies used to log in! If you went to facebook right now, and went to the developer console (chrome), under Application -> Cookies -> facebook.com, you would see this cookies you sent to facebook every request to identify you. When you open an incognito window and go to facebook, your browser is not sending these cookies, and therefore your facebook feed does not pop up.
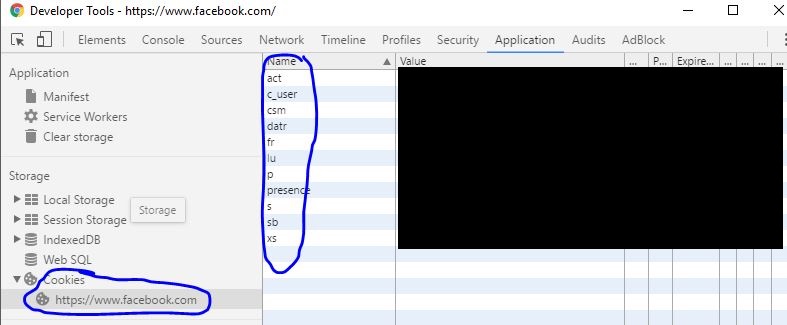
I can’t believe this, these aren’t real…why would these be sent like this…
I had to give it a try, I copied the cookies into vim, and wrote a quick macro that changed all the cookies to look like this:

I then hopped onto my VPN, opened an incognito window, went to facebook.com (showed the login page obviously), went to the cookies, cleared them all out, entered my formatted cookies into the console and hit refresh……..
It worked.
Up came my friend’s facebook page (who visited). I have full access to all of this person’s facebook account, messages, posts, etc. I of course realized this proof of concept and immediately exited and did nothing.
For those that are still confused: technically, this is just like session hijacking except with persistent cookies. I basically had all the details that made me look like this user, and sent them off to the server and it thought I was them. If you didn’t know, your cookies are very valuable and secret/private.
How did this happen?
Great question, I’m actually not quite sure. I’ve done some research, and I do know that this staticxx.facebook.com is part of facebook’s CDN. However this xd_arbiter I’m not entirely sure what it does.
This here may actually be the problem that I encountered, but it may also be a problem of the browser?? Because the browser is the one choosing to send the cookies, and it saw it to be fit to send all the identifying cookies when making this request.
If we look at the request again:

We see on the bottom that the “Referer” was espn.go.com. I had a suspicion that if you were logged into facebook on this site, and perhaps liked something, or shared it, or something, it would generate this plaintext request. However I tried and tried and tried so much to reproduce this result, but it was always redirected to sending the cookies over https. All the xd_arbiter.php requests were made securely (it mostly fetched the http version and it redirected to https before sending cookies). This again makes me feel like it could have been their browser (on mobile) that made a bad call of sending cookies when it shouldn’t have, because I was only testing it on chrome on my desktop, not under the exact conditions on which it occurred.
Seems like a quirk if I’ve ever seen one…but I happened to be listening at the right time, and found quite the gem. I am so curious to how it was originally produced though…
My Interaction With Facebook Bug Bounty Program
I had an interesting and slightly dismissive interaction with the facebook bug bounty program. They didn’t seem to understand or believe that I got full access to a facebook account just by listening to open wifi.
10/7/2016 – bug submitted
10/12/2016 – Facebook replied:
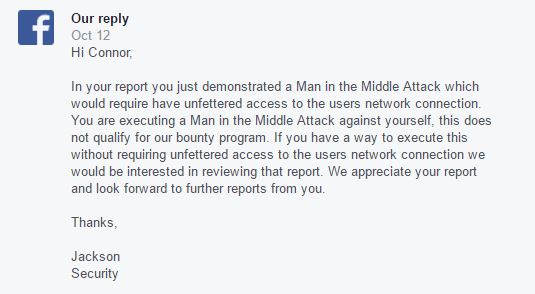
10/12/2016 I replied:
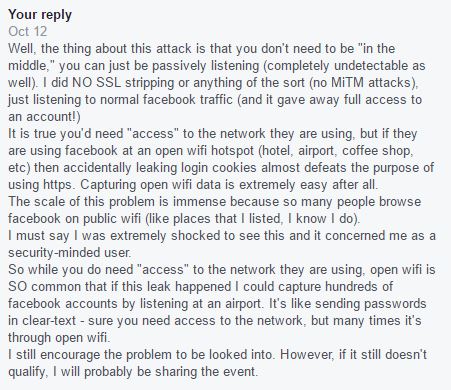
10/18/2016 they replied:
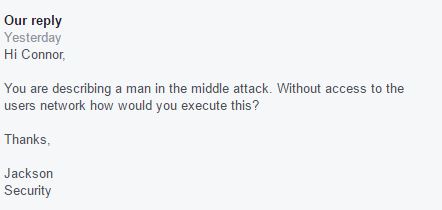
10/18/2016: I replied:
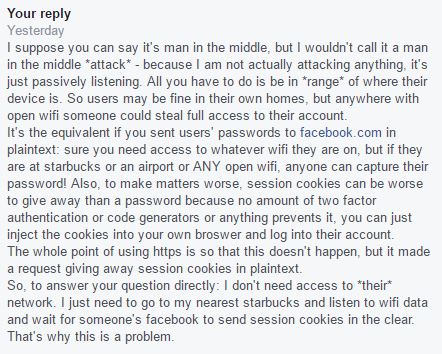
10/19/2016: They replied, I highlighted the correct parts in blue and the…incorrect parts in red.
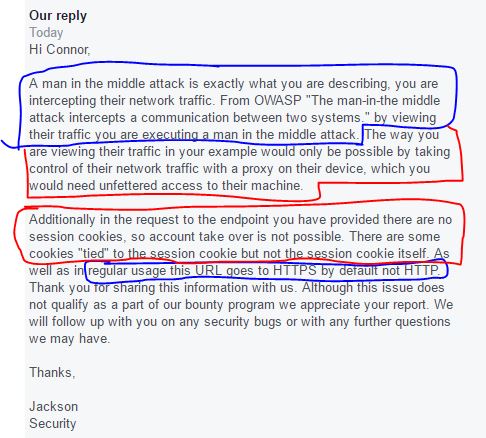
The reason why those are incorrect is because I did not need “full unfettered access” to their machine. I got the cookies just from listening to open wifi, without knowing anything or having any privileges on their device. Also, the cookies I captured did let me log in to their facebook, because I tried, and it worked. I detail this in my response:
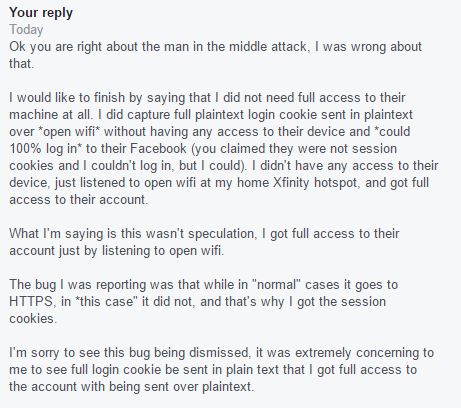
That is the most recent activity. I suppose the bug is closed now but I will update this if I get another response.
Please comment and let me know what you think, and how you think it happened.