Creating a separate network for public facing servers (DMZ)
A common practice for public facing servers is to have a totally separate network for the public facing servers so in the event of unauthorized privileged execution, the attacker won’t be able to access the precious internal network resources. This concept is called a DMZ (de-militarized zone). I decided to set this up myself because I love networking and it is something I always wanted to try. I configured and set it all up in a virtualized Xen environment on my 2 1U rack servers.
The Idea was simple, set something up like this:

(Yes there are a few mistakes in the diagram, the game server IP should be 10.2.0.11 and the DMZ router dhcp range should be 10.2.0.50-60)
There is a main firewall that forwards all public server ports (like port 80) to an internal virtualized pfsense router. This router is has two virtual interfaces, one to the private lan, and one to a virtual DMZ LAN.
So I just created two interfaces for the pfsense gateway:

I did have a slight problem getting this working. Aparently the Xen version I was using had some networking bug or some weird thing. Bottom line I had to run these CLI commands on the Xen Dom0 (Domain 0):
xe vif-param-set uuid=VIFUUID other-config:ethtool-gso="off"
xe vif-param-set uuid=VIFUUID other-config:ethtool-ufo="off"
xe vif-param-set uuid=VIFUUID other-config:ethtool-tso="off"
xe vif-param-set uuid=VIFUUID other-config:ethtool-sg="off"
xe vif-param-set uuid=VIFUUID other-config:ethtool-tx="off"
xe vif-param-set uuid=VIFUUID other-config:ethtool-rx="off"
Now the tricky part was configuring that gateway, because to my internal private LAN I was working on, this router saw it as the WAN and therefore couldn’t be configured through it. So I actually had to use a windows virtual machine on that internal DMZ network to configure the router. I configured the DMZ network to have a network of 10.2.0.0/24.
I then realized however, I could create a server inside this network to act as a VPN (what you see in the picture) so I can access all those internal DMZ resources, which is what I used from then on out. This is a one way tunnel though (of course, otherwise it would defeat the purpose). So I can access DMZ resources, but those servers cannot come back out.
There wasn’t much more to do, I just added a firewall rule for the VPN server, and a firewall rule to prevent internal DMZ clients from accessing anything on the private LAN (blocking 10.0.0.0/24)
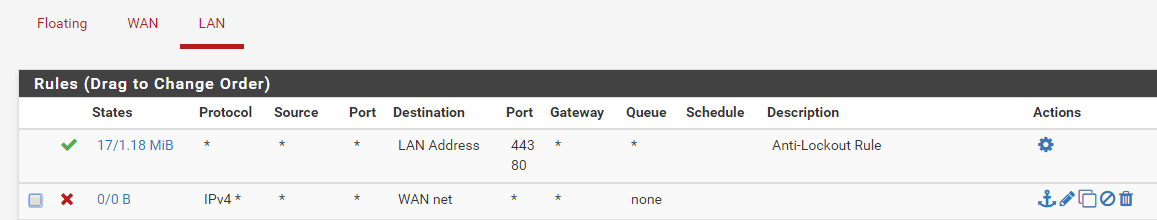

There! I now had a internal secure network for public facing servers with peace of mind that any internal resources (perhaps SAMBA shares or general purpose machines) cannot be accessed from it.